Understanding Privacy Risks: New Devices and Payment Security in 2026
Setting up a new smartphone creates critical vulnerability for financial data. Every saved payment method becomes a breach point. For Bigo Live users, this moment demands strategic decisions about transaction handling.
The stats are concerning: 39% of users encountered Bigo Live top-up scams, losing $200-$440 per incident. When you link cards to the Bigo app on new devices, you're granting persistent access to sensitive data that remains vulnerable throughout your device's lifecycle.
For high-volume regions, platforms like purchase Bigo coins United Arab Emirates offer browser alternatives that bypass card storage entirely, keeping credentials isolated from your phone's app ecosystem.
Why New Device Setup Is Critical
Your new phone arrives with zero stored credentials—a clean slate. Decisions during setup determine your privacy baseline for years. Installing Bigo Live and linking cards creates permanent data residency accessible through extensive app permissions.
Bigo requires iOS 13.0+ or Android 5.0+, but these systems grant apps extensive access once approved. Saved card details persist across updates, backups, and device transfers—creating exposure points browser transactions avoid completely.
Payment Security Threats in Live Streaming
Live streaming platforms face unique challenges due to real-time transactions and global bases. Payment systems must process instantly, creating pressure to streamline checkout—often sacrificing security.
App store commissions compound risks. iOS charges 30%, Android 15-30%, pushing users toward alternatives. Many choose convenience over security, storing cards without understanding long-term privacy implications.
How Bigo Users Face Payment Vulnerabilities
VPN usage blocks 10-20% of top-up attempts; network failures affect 26.3%. These barriers push users toward storing methods in-app for retry convenience, multiplying vulnerability with each saved credential.
Decline rates spike for purchases exceeding $100—30% fail, risk checks increase 68.5%. Users save multiple methods to ensure success, creating comprehensive financial databases on devices—exactly what privacy-conscious users should avoid.
Hidden Risks of Linking Cards to New Phones
When you save card details in Bigo and tap save for future, you initiate complex storage extending beyond convenience. Your info becomes encrypted in the app's container, but security depends on implementation quality, OS integrity, and backend systems.
What Happens When You Save Cards
Saved credentials create persistent data objects in app storage. Unlike browser transactions that process and discard data, in-app storage maintains card number, expiration, CVV, and billing address in encrypted databases. This becomes a malware target, vulnerable if your device is compromised, accessible through backups that may lack equivalent encryption.
Reality: your secure card data syncs across cloud backups, transfers during migrations, remains accessible to updates introducing new vulnerabilities. Each touchpoint represents breach vectors that don't exist with browser-based, one-time processing.
App Permission Overreach
Installing Bigo grants permissions beyond payment processing. While necessary for camera/microphone during broadcasts, these create broader attack surfaces when combined with stored payment data. A compromised app with extensive permissions can access stored credentials, contacts, location, and files simultaneously.
Browser top-ups require zero app permissions for payment. Your BIGO ID—8-10 digits like 901873661—serves as the only connection. This ID remains consistent across platforms, enabling transactions through mobile.bigo.tv/live/bigolivepay/index.html without granting payment permissions to the app.
Real Breach Impact
The 39.7% increase in risk checks reflects industry-wide security concerns. Users storing methods in-app become collateral damage when platform incidents occur, as saved credentials join compromised databases.
Payment failures affect 30% of high-value transactions, but recovery for compromised stored cards creates greater disruption: contact issuers, dispute charges, receive replacements, update across all services—cascading inconvenience browser methods prevent.
Device Loss Scenarios
Lost/stolen phones with saved Bigo payments create immediate financial risk. Even with encryption and lock screens, attackers exploit vulnerabilities to access app data. Browser approaches eliminate this—your device contains zero stored credentials, making theft hardware loss rather than financial crisis.
Recovery requires immediate card cancellation even without unauthorized charges, disrupting financial access across all services. Browser-only users face no such complications.
Browser-Based Bigo Top-Up: Privacy-First Alternative
Browser purchases restructure payment security. Instead of storing credentials, you process each transaction through secure web gateways handling data server-side. Your phone serves as interface only, never storing financial info locally.
This leverages HTTPS SSL encryption and PCI-DSS compliance. Visiting mobile.bigo.tv through your browser processes transactions in isolated environments separate from app ecosystems. Your BIGO ID connects payment to account without password entry, OTP, or authentication storing credentials locally.
For multi-region accounts, services offering recharge Bigo Live diamonds Saudi Arabia through browsers provide consistent security regardless of location or device.
How Browser Payments Work
Process begins with your BIGO ID—numerical identifier under profile nickname when tapping Me bottom-right. This 8-10 digit number (without ID: prefix) serves as unique account identifier. Enter it in UID field on legitimate sites like bigo.tv or mobile.bigo.tv.
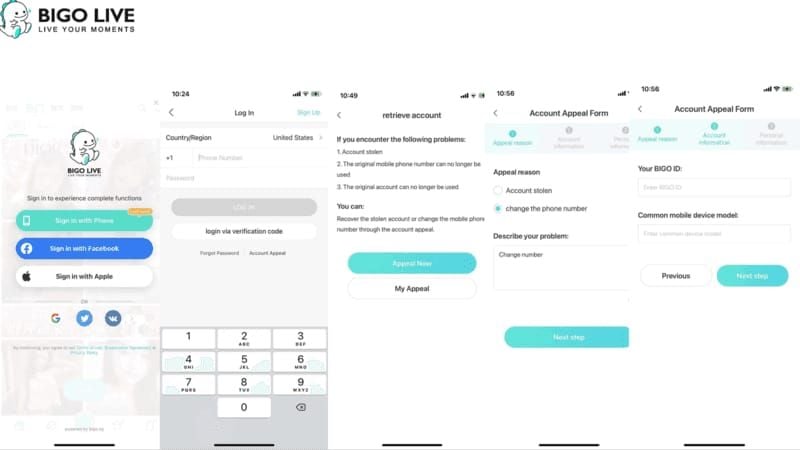
After entering ID, select diamond package and proceed to payment. Unlike in-app purchases saving cards, browser transactions process through secure gateways not storing credentials on devices. Processors handle card data server-side, complete transactions, credit diamonds—all without creating persistent payment data on phones.
Delivery is fast: 98% credit within 3 minutes, average 8 seconds. After browser purchase, navigate to Me > Wallet and refresh 3-5 times, or relog after 0-5 minutes to verify.
Security Architecture
Browsers implement sandboxing isolating each session from device core systems and other apps. Processing Bigo top-ups through browsers occurs within protected environments, preventing payment data from touching file systems or app storage layers.
This isolation means even if malware infects devices, it can't access credentials never stored locally. Browser transactions exist as temporary sessions terminating upon completion, leaving zero residual data for attackers—stark contrast to in-app stored cards persisting as encrypted but extractable objects.
Payment Tokenization
Secure browser gateways employ tokenization—replacing actual card numbers with single-use tokens per transaction. Tokens process payments but become worthless after use, preventing replay attacks if intercepted. Combined with SSL encryption protecting data in transit, browser transactions create multiple security layers in-app cards can't match.
Implementation ensures card numbers never appear in plain text on devices. From entry to confirmation, encryption protects data flow. Browser cache may temporarily store session cookies, but these contain no payment credentials and expire automatically.
No App Permissions Required
Browser top-ups require zero additional permissions beyond internet access. You don't grant Bigo access to payment systems, storage, or device identifiers. Your BIGO ID serves as sole connection, maintaining complete separation between financial data and app permission scope.
This minimization dramatically reduces attack surface. Even if Bigo experiences vulnerabilities, payment info remains protected because it never existed within the app's accessible data environment.
Step-by-Step: Topping Up via Browser on New Devices
Secure browser top-ups require specific steps maximizing privacy while ensuring delivery. This works identically on new or established devices.
Prerequisites
Locate your BIGO ID through the app. Open Bigo Live, tap Me bottom-right, view BIGO ID under profile nickname. Or tap profile avatar, hit Edit pen icon, scroll to BIGO ID section. Record this 8-10 digit number.
Ensure stable internet—at least 5Mbps Wi-Fi. Avoid VPNs during top-ups; VPN connections block 10-20% of transactions. Your device needs modern browser with current security certificates—Chrome, Safari, or Firefox work.
Finding Secure Platforms
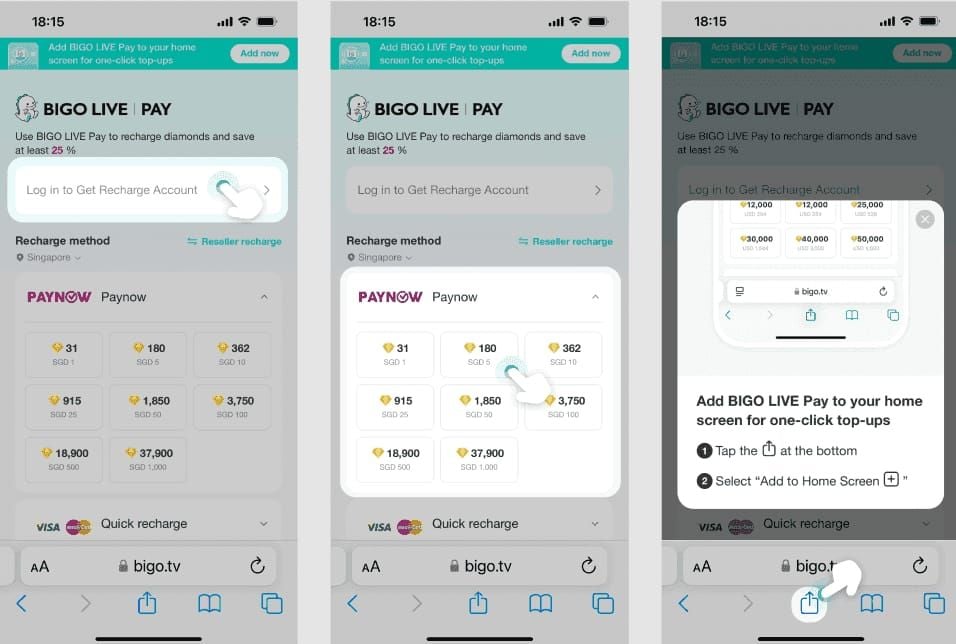
Navigate to official URLs: mobile.bigo.tv/live/bigolivepay/index.html or main bigo.tv domain. Always verify HTTPS before entering info. Legitimate platforms display SSL certificates and secure connection indicators.
For enhanced security and competitive pricing, BitTopup offers trusted browser platform designed for privacy-conscious users. Maintains PCI-DSS compliance, implements advanced encryption, processes transactions without app installation or device permissions. Delivers same 37.5% savings vs iOS in-app while maintaining industry-leading security.
Complete Transaction Walkthrough
- Open browser in incognito/private mode
- Navigate to secure platform (mobile.bigo.tv or BitTopup)
- Enter BIGO ID in UID field—numerical digits only, omit ID: prefix
- Select desired diamond package
- Choose payment method from secure gateways
- Complete payment through processor's secure interface
- Receive confirmation—don't close browser until confirmation appears
Process typically completes under 45 seconds using high-success methods like PayPal (90% success, 45-second average). Transaction limits: daily cap 10,000 diamonds, 5-minute intervals between recharges, max 3 retry attempts per session.
Verifying Balance
After browser transaction, open Bigo app, navigate to Me > Wallet. Refresh 3-5 times by pulling down. If diamonds don't appear, wait 0-5 minutes and relog. 98% delivery within 3 minutes means most credit instantly, 95% process under 5 minutes.
If diamonds haven't appeared after 5 minutes, verify BIGO ID was entered correctly. ID remains consistent across platforms, so discrepancies indicate data entry errors. Contact payment platform customer service with transaction confirmation—BitTopup offers excellent support for delivery concerns.
Troubleshooting
Payment declines occur in 30% of transactions exceeding $100 due to fraud prevention. If purchase fails, try smaller denomination or alternative method. Avoid rapid retries; this triggers additional risk checks increasing decline probability 68.5%.
Network failures affect 26.3% of transactions. If experiencing connection errors, verify Wi-Fi meets 5Mbps minimum, disable VPNs. Switch to incognito mode if you haven't—prevents cached data conflicts interfering with processing.
For persistent issues, clearing browser cache resolves 70-80% of Android problems, 95% of iOS difficulties. Navigate to Settings > Apps > Browser > Storage > Clear Cache, relog after 10 minutes.
Privacy Comparison: Browser vs In-App
Data Exposure Analysis
Browser-Based:
- Payment credentials processed server-side, zero local storage
- BIGO ID only persistent data on device
- Transaction history stored remotely, not in app
- No payment method saved
- Session data auto-cleared after completion
- Device loss exposes no financial info
In-App Linking:
- Full card details encrypted in app container
- Methods persist across updates and backups
- Transaction history stored locally and remotely
- Saved cards remain until manually removed
- Backups may maintain payment data indefinitely
- Device loss requires immediate card cancellation
Fundamental difference: browser creates temporary sessions leaving zero residual data; in-app creates persistent financial objects vulnerable throughout device lifecycle.
Permission Requirements
Browser top-ups require no payment-specific permissions. Browser needs only internet access—baseline for all connected apps. Bigo never receives payment processing permissions, storage access for financial data, or device identifier access for transaction tracking.
In-app purchases require granting Bigo permission to access payment systems, store data in secure containers, potentially access device identifiers for fraud prevention. Each additional permission creates potential vulnerability if app experiences compromises.
Security Ratings
Browser platforms implementing HTTPS SSL and PCI-DSS compliance achieve highest security ratings. Isolation architecture prevents cross-contamination between payment data and device systems; tokenization ensures intercepted data can't be reused.
In-app purchases rely on app security implementation quality, varying based on development practices and update frequency. The stored credential model inherently creates more exposure points than browser alternatives. The 39% scam rate demonstrates current measures don't fully protect against all threats.
Long-Term Implications
Choosing browser top-ups establishes privacy-first baseline with compounding benefits. Each transaction maintains zero data residency, preventing gradual accumulation characterizing in-app approaches. Over time, browser users maintain clean devices with no payment exposure; in-app users accumulate multiple saved cards.
Compounding extends to device upgrades. Users never storing methods in apps can transfer to new phones without worrying about payment migration, backup security, or credential cleanup on old devices.
Expert Tips for Maximum Security
Setting Up New Phones
Configure with minimal app installations initially. Before installing Bigo, establish browser top-up workflow using bookmarks to official URLs. This ensures you never feel pressured to store methods in-app—browser workflow is already established and equally convenient.
Enable device encryption and strong lock screen security before installing apps handling sensitive data. Two-factor authentication reduces scams by 90%, making it essential for accounts regularly processing purchases.
Using Virtual Cards
Virtual card services generate single-use or limited-use numbers linking to actual credit accounts. Using virtual cards for browser Bigo top-ups creates additional isolation—even if transaction data were compromised, virtual numbers become worthless after use or reach preset limits.
Works well for regular purchases. Generate new virtual cards per transaction or create monthly-limit cards that auto-expire, preventing unauthorized recurring charges. Combined with browser processing, virtual cards deliver maximum security.
Two-Factor Authentication
Enable 2FA on Bigo immediately after setup. Protects against unauthorized access even if passwords are compromised. For users processing regular purchases, 2FA prevents account takeover where attackers could access transaction history or attempt fraudulent purchases.
Use authenticator apps rather than SMS-based 2FA when possible. Authenticator apps generate time-based codes not relying on cellular networks, eliminating SIM-swapping vulnerabilities.
Regular Security Audits
Conduct monthly reviews of transaction history through Me > Wallet. Verify all diamond purchases match actual transactions—check dates, amounts, methods. Any discrepancies warrant immediate investigation and password changes.
Monitor payment statements for unauthorized Bigo charges. While browser top-ups minimize this risk, regular verification ensures you catch issues immediately. Set up transaction alerts through banks for real-time notification.
Managing Multiple Devices
Users accessing Bigo across multiple devices should maintain consistent browser top-up practices on all phones and tablets. Your BIGO ID works identically across platforms, enabling purchases from any device's browser without storing methods on any of them.
Avoid storing cards on primary devices for convenience. This creates inconsistent security undermining privacy-first approaches. Maintaining browser workflows across all devices ensures uniform security regardless of which phone you're using.
Common Misconceptions
Myth: In-App Is More Convenient
Many assume saving cards creates superior convenience. Reality: browser top-ups require only BIGO ID and take under 45 seconds—virtually identical to in-app stored card purchases. Perceived convenience doesn't account for time managing stored methods, updating expired cards, or dealing with security incidents.
Browser bookmarks to official URLs create one-tap access matching in-app convenience while maintaining zero stored credentials. Modern browsers autofill BIGO ID after first use, eliminating repetitive entry.
Myth: Browser Payments Are Slower
Processing speed depends on gateway efficiency, not browser vs app. The 98% delivery within 3 minutes for browser top-ups matches or exceeds in-app speeds. Average 8-second delivery demonstrates browser transactions process nearly instantaneously.
PayPal browser transactions maintain 90% success with 45-second average—faster than many in-app flows requiring multiple screens, selecting saved cards, and confirming purchases.
Myth: Linked Cards Are Safer
Some believe saved cards undergo enhanced verification for subsequent purchases. Opposite is true: stored credentials create persistent vulnerability that doesn't exist with fresh browser transactions. Each saved card use accesses data stored since initial entry—exposed to every update, backup, and potential incident during that period.
Browser transactions process each purchase through current security protocols with fresh encryption and tokenization, ensuring you benefit from latest standards every time.
Truth: Expert Recommendations for 2026
Security professionals consistently recommend minimizing stored credentials across all platforms. Data minimization—storing only essential info for shortest necessary duration—contradicts the saved card model. Browser-based, one-time processing aligns perfectly with expert recommendations.
For live streaming specifically, experts emphasize separating payment processing from app ecosystems. The 39% scam rate demonstrates current measures require supplementation through user-side best practices. Browser top-ups represent the most effective user-controlled security enhancement available.
Why BitTopup Is the Trusted Choice
BitTopup has established itself as premier platform for users prioritizing payment security without sacrificing convenience or competitive pricing. Architecture specifically addresses privacy concerns making browser top-ups essential for new devices.
Advanced Security Features
BitTopup implements comprehensive measures including HTTPS SSL encryption for all data transmission and full PCI-DSS compliance for payment processing. Industry-standard protections ensure financial info receives bank-level security throughout transactions. Security architecture prevents payment data from ever touching device local storage.
Two-factor authentication options provide additional account protection, while advanced fraud detection monitors transactions without creating false positives blocking legitimate purchases. Balanced approach delivers security without excessive decline rates—maintains high success even for larger packages.
Browser Transaction Process
Streamlined interface requires only BIGO ID and payment selection. Design eliminates unnecessary steps while maintaining essential security verifications. After entering 8-10 digit ID, select from competitively priced packages and proceed directly to secure processing.
Supports multiple payment methods with varying success rates and speeds, letting you choose options matching preferences. High-reliability methods like PayPal integrate seamlessly, delivering 90% success and 45-second processing making browser transactions as fast as in-app.
User Experience
Interface design prioritizes efficiency for repeat users. Platform remembers BIGO ID across sessions (stored server-side, not on device), enabling one-click package selection for subsequent purchases. Convenience matches saved card workflows while maintaining zero local credential storage.
Mobile-optimized design ensures smooth transactions on new phones regardless of screen size or OS. Responsive interface adapts to iOS 13.0+ and Android 5.0+ devices, delivering consistent experiences across platforms.
Customer Protection
Maintains comprehensive protection policies addressing delivery failures, transaction disputes, and account issues. Excellent customer service provides responsive support for rare instances when transactions don't complete within standard timeframes.
Transaction guarantees ensure you receive purchased diamonds or full refunds—no partial credits or platform-specific currencies limiting options. Combined with competitive pricing delivering 37.5% savings vs iOS in-app, BitTopup offers compelling value for privacy-conscious users.
Maintaining Payment Privacy: Best Practices for 2026
Regular Security Checklist
Monthly:
- Review transaction history in Me > Wallet for unauthorized purchases
- Verify payment statements for unexpected Bigo charges
- Update Bigo app to latest version for security patches
- Check for unusual account activity or login attempts
- Confirm 2FA remains enabled and functioning
Quarterly:
- Audit browser bookmarks to ensure top-up URLs remain official
- Review device permissions granted to Bigo Live app
- Update device OS for security improvements
- Change Bigo password using strong, unique credentials
- Verify backups don't store payment-related data
Annual:
- Comprehensive security review of all devices accessing Bigo
- Evaluation of payment methods for potential virtual card adoption
- Assessment of emerging threats affecting live streaming platforms
- Review of BitTopup or alternative platform security certifications
Auditing Payment Methods
Create inventory of all devices accessing your Bigo account. For each, document whether payment methods are stored in-app and schedule removal if found. This reveals security gaps where stored credentials create unnecessary vulnerability.
Verify browser top-up workflows are established on all devices. Bookmark official URLs on each browser, ensuring you never face situations where in-app payment seems like the only convenient option.
Staying Updated on Threats
Follow security news covering mobile payment vulnerabilities and live streaming incidents. Understanding emerging threats helps you adapt practices proactively. Subscribe to Bigo's official security announcements for platform-specific updates about new protections or identified vulnerabilities.
Monitor changes to payment processing regulations in your region. Privacy laws evolve rapidly, and new protections may offer additional safeguards for browser transactions.
Building Long-Term Strategy
Commit to browser top-ups as permanent approach rather than temporary measure. Consistency prevents security gaps emerging when users alternate between secure and less-secure methods. Establish BitTopup or another trusted platform as exclusive source, creating predictable transaction patterns making unauthorized charges immediately obvious.
Document your workflow in secure note accessible across devices. Include BIGO ID, preferred platform URLs, and step-by-step instructions. This helps maintain consistent practices when switching devices or after extended periods without purchases.
Consider setting monthly diamond budget and processing single larger purchase rather than multiple small transactions. Minimizes frequency of payment data transmission while taking advantage of better per-diamond pricing on larger packages. Daily cap of 10,000 diamonds accommodates substantial monthly budgets within single transactions.
FAQ: Browser-Based Bigo Top-Up and Privacy
Is it safer to top up Bigo through browser or mobile app?
Browser top-ups are significantly safer because they process payments without storing credentials on devices. Payment info exists only during transaction sessions, handled server-side by secure gateways. In-app purchases require storing card details in app encrypted containers, creating persistent data vulnerable to device compromise, malware, or theft. The 39% scam rate demonstrates minimizing stored payment data reduces overall risks.
What are privacy risks of linking cards to new phones?
Linking cards creates multiple exposure points: stored credentials accessible through app permissions, vulnerable to extraction if devices are compromised, persist across backups and transfers. Device loss/theft requires immediate card cancellation even without confirmed unauthorized charges. Stored cards grant apps ongoing payment system access extending beyond single transactions, creating persistent vulnerability throughout device lifecycles.
How does browser-based top-up protect payment information?
Browser transactions use HTTPS SSL encryption and PCI-DSS compliant gateways processing card data server-side without local storage. Payment tokenization replaces actual card numbers with single-use tokens becoming worthless after completion. Browser sandboxing isolates payment sessions from device app ecosystems and file systems, preventing payment data from touching local storage. Zero residual financial data remains on phones after purchases.
Can I buy Bigo diamonds without giving app payment permissions?
Yes—browser top-ups require only your BIGO ID, an 8-10 digit numerical identifier visible in your profile. Enter this ID on secure platforms like mobile.bigo.tv or BitTopup, select diamond package, complete payment through browser gateways. Bigo app never receives payment processing permissions, storage access for financial data, or payment-related device permissions. Diamonds credit within 3 minutes despite app having zero payment system access.
Does browser top-up work as fast as in-app purchases?
Browser top-ups deliver 98% of orders within 3 minutes with average 8-second processing—matching or exceeding in-app speeds. High-efficiency methods like PayPal maintain 90% success with 45-second average processing. Speed difference between browser and in-app is negligible, while security advantages remain substantial. After browser purchase, refresh wallet 3-5 times or relog after 0-5 minutes to verify delivery.
What payment method offers best privacy for Bigo users in 2026?
Browser top-ups using virtual cards provide maximum privacy. Virtual cards generate single-use or limited-use numbers linking to actual credit accounts, creating additional isolation beyond browser security. Process purchases through platforms like BitTopup implementing HTTPS SSL and PCI-DSS compliance, using incognito browser mode with 5Mbps Wi-Fi and no VPN. This delivers bank-level security with zero stored credentials, 37.5% cost savings vs iOS in-app, and fast delivery within standard 3-minute timeframes.
Protect your privacy while enjoying Bigo Live—top up diamonds securely through BitTopup's browser platform. No card linking, no app permissions, just fast and safe transactions with competitive pricing saving you 37.5% vs in-app purchases. Start your secure top-up now and experience peace of mind with every purchase.