Understanding Chamet Device Bans
Chamet device bans blacklist specific hardware identifiers, preventing any account from accessing the platform on that device—different from temporary account suspensions.
What Hardware IDs Are and Why Chamet Uses Them
Hardware IDs are unique alphanumeric codes permanently embedded in device components during manufacturing. Chamet collects these to combat fraud and ban evasion:
- IMEI numbers (International Mobile Equipment Identity)
- MAC addresses for network adapters
- Android IDs
- Device serial numbers
Account-level bans proved insufficient since violators created new accounts. Hardware flagging ensures serious violators can't immediately return. For secure transactions, BitTopup offers chamet diamonds recharge without compromising device authentication.
Chamet's Multi-Layer Device Fingerprinting
Chamet creates composite device profiles by tracking:
- IP addresses for network locations
- Facial recognition with blink detection during registration
- Behavioral patterns across sessions
- Multiple hardware signatures cross-referenced against blacklist databases
Chamet's AI detects ban issues in 3-15 minutes after suspicious activity. Even if one identifier changes, remaining data points create recognizable patterns triggering enforcement.
Account Ban vs Device Ban
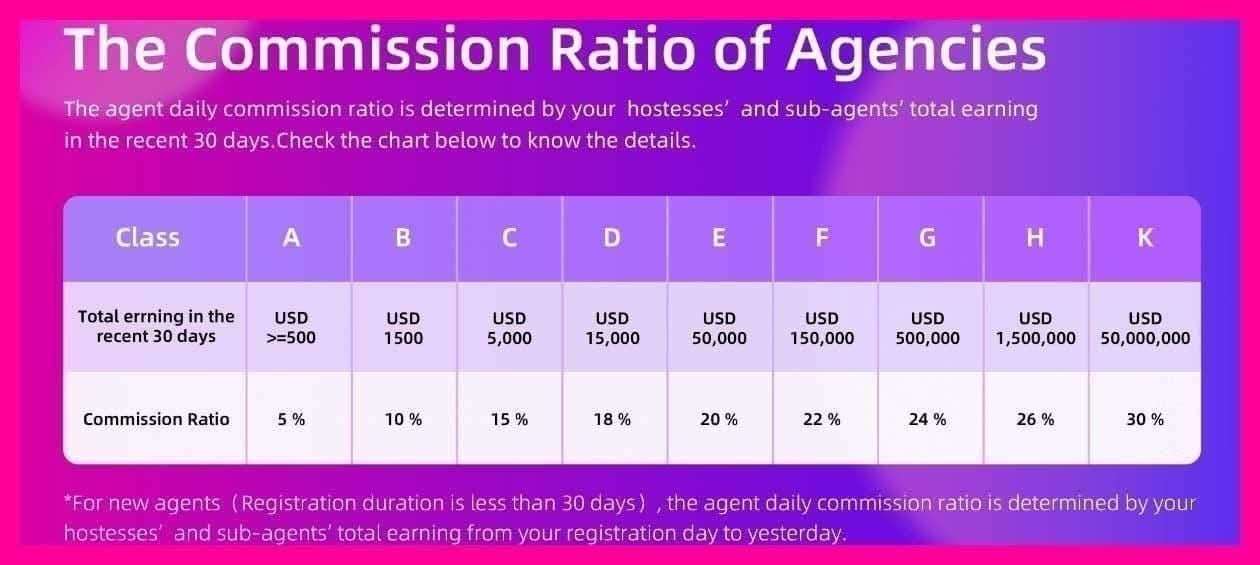
Account bans restrict specific Chamet profiles while leaving devices eligible for new accounts. Typically result from minor violations, lasting 24-48 hours. Statistics show 67.6% of bans stem from community guideline violations.
Device bans blacklist hardware entirely. No account functions on banned phones regardless of registration status. January 3, 2025 guidelines update targeted explicit mods and unauthorized modifications, increasing device-level enforcement.
What Factory Reset Actually Clears
Factory reset wipes user data and configurations but leaves hardware identifiers untouched.
Android Data Wiped by Factory Reset
- Downloaded apps including Chamet
- Google account associations
- Photos and documents in internal memory
- App caches and login credentials
- System settings (returns to manufacturer defaults)
Reset clears Android ID (64-bit randomly generated number) and may regenerate Google Services Framework ID—but these represent a small fraction of Chamet's tracking arsenal.
Persistent Hardware Identifiers
Hardware identifiers remain permanently encoded in physical components:
- IMEI number: Burned into baseband processor during manufacturing
- MAC addresses: Hardcoded into Wi-Fi/Bluetooth chips
- Serial number: Assigned in device firmware
- Build properties: Manufacturer name, model, hardware revision accessible through Android APIs
IMEI, MAC Address, Serial Number Permanence
IMEI serves as your phone's permanent DNA—15-digit code identifying devices on cellular networks. Chamet accesses this through standard Android permissions. Changing IMEI requires rooting and specialized software, violating telecommunications laws in most countries and voiding warranties.
MAC addresses remain constant across software changes. Even with Wi-Fi disabled, Bluetooth MAC provides another permanent identifier.
Serial numbers accessible through Android's Build.SERIAL API complete this trinity of unchangeable markers Chamet monitors.
Factory Reset Process for Android
While reset won't remove bans, here's the proper procedure:
Backup Data First
- Navigate to Settings > System > Backup for automatic Google backup
- Transfer photos/videos to cloud or computer
- Export documents from Downloads folder
- For Chamet: Record wallet balance (Profile > Earnings > My Wallet) and 8-12 digit User ID (Profile > My Profile)
Performing Factory Reset

- Open Settings > System or General Management
- Select Reset Options > Erase all data (factory reset)
- Review warning listing deleted data
- Enter device PIN/pattern/password
- Tap Erase everything or Reset phone
- Device restarts, displays Android boot animation for 5-15 minutes
Post-Reset Configuration
- Select language and region
- Connect to Wi-Fi
- Sign in with Google account (restoration takes 10-30 minutes)
- Reinstall apps automatically if backup enabled
- Sign in to each service individually
If you install Chamet on a device-banned phone, fingerprinting immediately recognizes hardware identifiers and prevents access, confirming reset had no effect.
Does Factory Reset Remove Chamet Bans? No.
Factory reset doesn't remove Chamet device bans because it operates at the wrong technical layer.
Real-World Test Results
Community reports show users who factory reset encounter immediate ban enforcement—often during initial app loading or SMS verification. While 60% of technical glitches resolve through device restarts within 30 minutes, these statistics apply to temporary errors, not deliberate device bans.
Why Factory Resets Fail
Resets operate at software level. Chamet targets hardware identifiers in firmware and physical components. Even if reset altered one identifier (it doesn't), remaining markers create recognizable patterns triggering enforcement.
Chamet's Detection System
When you launch Chamet:
- App queries hardware identifiers through Android APIs (milliseconds)
- Collected data (IMEI, MAC, serial, build properties) transmits to servers
- AI processes info in 3-15 minutes, cross-referencing against ban database
- Partial matches flag installation and prevent access
For account management during recovery, BitTopup provides reliable top up chamet app services maintaining transaction security, though recharging won't circumvent device bans.
Hardware Identifiers Chamet Tracks
IMEI and MEID
IMEI (GSM devices) and MEID (CDMA networks) are 14-15 digit codes in baseband processors. Chamet accesses via READ_PHONE_STATE permission. Changing IMEI violates U.S. federal law (18 U.S.C. § 1029) and similar regulations globally.
Android ID and Google Services Framework ID
Android ID: 64-bit hexadecimal string regenerating after factory reset. Chamet doesn't rely on this as primary identifier due to volatility.
GSF ID: Regenerates under certain conditions but serves as supplementary tracking point only.
MAC Address, Bluetooth ID, Network Signatures
Wi-Fi MAC address: 12-character hexadecimal identifier hardcoded in network chip. Accessible through ACCESS_WIFI_STATE permission.
Bluetooth MAC: Separate identifier accessible even when Bluetooth disabled.
Network signatures: Connection patterns (signal strength, timing) create additional fingerprint data.
Device Build Properties
Android's Build class provides:
- Manufacturer name (Build.MANUFACTURER)
- Device model (Build.MODEL)
- Hardware revision (Build.HARDWARE)
- Bootloader version (Build.BOOTLOADER)
- Serial number (Build.SERIAL - restricted in Android 8.0+)
Combined with unique identifiers, these strengthen fingerprinting accuracy and persist across resets.
Common Misconceptions
Myth: Factory Reset Gives Clean Slate
Reality: Chamet's ban enforcement maintains server-side database of banned hardware identifiers. Your phone's permanent markers remain unchanged, so reinstalling Chamet reads same identifiers and checks against ban database. Clean slate exists only at software level.
Myth: VPN Hides Device Identity
Reality: VPNs mask IP but don't affect hardware identifiers Chamet reads directly from devices. App queries IMEI, MAC addresses before network communication. 90% of appeal denials involve VPN usage—platform interprets this as evasion attempts.
Myth: Changing Google Account Removes Ban
Reality: Chamet's fingerprinting operates independently of Google accounts. Platform monitors hardware identifiers constant regardless of which Google account you use. Account-switching accomplishes nothing.
Truth About Custom ROMs and Root
Custom ROMs/rooting provide deeper system access but carry significant risks with limited effectiveness. Can't alter hardware-encoded IMEI/MAC without specialized modifications. Chamet likely detects rooted devices, flagging them as security risks. May 2025 tightened scan rules and August 2023 ban on unofficial APKs demonstrate increasing scrutiny. v3.1.1 update fixed 61 vulnerabilities related to detecting tampered installations.
Legitimate Recovery Alternatives
Contact Chamet Official Support

Submit ban appeals within 7 days to chamet.feedback@gmail.com. Standard responses arrive in 24-48 hours; complex cases take 3-5 days.
Include in appeal:
- 8-12 digit User ID (Profile > My Profile)
- Exact ban date/time
- Detailed activity explanation before ban
- Evidence demonstrating error vs intentional violation
- Respectful, factual tone
Required Documentation
- Screenshots of ban notification
- Account profile showing user history/level
- Transaction records (demonstrates account legitimacy)
- Communication with users potentially misinterpreted
Face verification processes in 24-48 hours (up to 72 during peak). SMS verification completes in 2-3 minutes. For follow-ups after 72 hours, contact chametservice@gmail.com.
Use Different Physical Device
Only reliable workaround if appeal denied. Requires phone with different hardware identifiers—not factory-reset version of banned device.
Setup tips:
- Don't use same Wi-Fi immediately (Chamet tracks IPs)
- Create fresh account vs logging into banned account
- Ensure device never had Chamet installed previously
- Contact support before logging in if recovering unbanned account
Appeal Timeline and Success Rates
Success varies by circumstances. First-time minor offenders see higher approval than repeat/serious violators. VIP users receive 400% faster replies (expedited processing, not guaranteed approval).
Legitimate cases resolve within 24-48 hours. Complex cases extend to 3-5 days. Approved device bans lift within 24 hours—restart device and clear Chamet cache before logging in.
Prevention Strategies
Community Guidelines and Terms
January 3, 2025 update banned explicit mods and unauthorized modifications. Access Chamet exclusively through official app stores. August 2023 policy banning unofficial APKs strictly enforced.
Prohibited behaviors:
- Harassment/abusive language
- Explicit content violating standards
- Multiple accounts manipulating rankings/rewards
- Automation tools/bots generating artificial engagement
- Off-platform transactions circumventing payment systems
Behaviors Triggering Automatic Flagging
- Rapid account creation/deletion patterns
- Multiple device logins across different locations quickly
- Unusual transaction patterns (large diamond transfers from multiple new accounts)
- Bypassing facial recognition/blink detection during registration
- VPN/proxy use during registration/regular use
Safe Account Management
- Single account per device, consistent geographic location
- Complete verification promptly (SMS in 2-3 minutes)
- Accurate, up-to-date profile information
- Authentic engagement vs scripted messages
- Gradual level building through genuine interaction
Secure Recharge via BitTopup
Use reputable platforms not requiring account credentials. BitTopup offers secure Chamet diamond recharge with competitive pricing, fast delivery, excellent customer service. Transaction protocols don't require Chamet password, reducing compromise risk.
Avoid unofficial sellers with suspicious prices—often involve stolen payment methods triggering security systems.
Safe Diamond Recharge During Recovery
Why BitTopup Is Safest
- Never requests Chamet password—only User ID (publicly visible)
- Competitive pricing reflecting legitimate wholesale rates
- Fast delivery (minutes after purchase)
- 24/7 customer support
- High user ratings across review platforms
Protecting Investment During Appeals
Don't purchase diamonds until appeal resolves—can't access platform to use them. Wait for official ban lift confirmation. If using different device, verify full account access before recharging.
Test functions before purchasing:
- View profile
- Access wallet (Profile > Earnings > My Wallet)
- Send test message
Transaction Security Best Practices
- Verify HTTPS encryption (padlock icon in browser)
- Double-check User ID before purchase
- Save confirmation emails/receipts
- Never share Chamet password with anyone
- Monitor account for delivery (5-15 minutes for reputable platforms)
Expert Action Plan
Immediate Steps After Ban
- Document everything: Screenshot ban notification, note exact date/time, record activity before ban
- Assess ban scope: Try logging in from different device—determines device-specific vs account ban
- Prepare appeal within 7 days: Gather User ID, transaction history, supporting evidence. Submit to chamet.feedback@gmail.com with clear, factual explanation
Long-Term Security Checklist
- Review community guidelines, eliminate triggering behaviors
- Understand VPN usage correlates with 90% appeal denials
- Implement safe practices: single account, consistent location, prompt verification, authentic engagement
- Consider VIP status for 400% faster support (professional users)
- Establish relationship with BitTopup before urgent needs
New Device vs Appeal Decision
Consider new device if:
- Appeal denied and Chamet essential for livelihood/connections
- Significant account investment (high level, diamond purchases, follower base)
- Budget devices available for $100-150
Accept ban if:
- Casual/recreational usage
- Ban resulted from legitimate violations
- Platform value doesn't justify expense
New device setup:
- Complete separation from banned device
- Different network initially
- Careful account setup avoiding linking algorithms
- Fresh account if previous banned; gradual authentic building
FAQ
Can factory reset change IMEI?
No. IMEI is permanently encoded in baseband processor during manufacturing. Factory reset only affects software/user data. Changing IMEI requires specialized equipment and violates telecommunications regulations.
How long do device bans last?
Typically permanent unless successfully appealed. Unlike temporary account bans (24-48 hours) or minor infractions (5 minutes-24 hours), device bans are Chamet's most severe action. Regain access via successful appeal (chamet.feedback@gmail.com, 24-48 hour response) or different physical device.
What data does Chamet collect?
IMEI/MEID, Wi-Fi/Bluetooth MAC addresses, serial numbers, Android ID, Google Services Framework ID, build properties (manufacturer, model, hardware revision), IP tracking, facial recognition with blink detection, behavioral pattern analysis. Multi-layer fingerprinting persists across software changes.
Can I use Chamet on new phone if old device banned?
Yes. Different physical device with different hardware identifiers allows access. Ensure new device never had Chamet installed; avoid same Wi-Fi initially. If account (not just device) banned, create new account. If only device banned, contact support before logging into existing account.
Does VPN help with device bans?
No. VPNs mask IP but can't hide hardware identifiers Chamet reads directly. 90% of appeal denials involve VPN usage—interpreted as evasion attempts. Using VPN during appeals typically results in permanent ban and rejection.
How to safely recharge during recovery?
Wait until appeal resolved and full access confirmed. Use reputable platforms like BitTopup (never request password—only User ID). Verify HTTPS encryption, double-check User ID. If using different device, test all functions (profile, wallet, messaging) before purchasing diamonds.
Protect your Chamet investment! Recharge safely with BitTopup - trusted platform for secure diamond purchases. Instant delivery, competitive rates, 24/7 support. Visit BitTopup now!